39 aws best practices
aws.amazon.com › blogs › mtBest Practices for Organizational Units with AWS Organizations In this post, we walk you through the elements of building a secure and productive multi-account AWS environment, often referred to as a "landing zone," as recommended by AWS. This represents the best practices that can be used to build an initial framework, while still allowing for flexibility as your AWS workloads increase over time. Best practices for working with AWS Lambda functions Best practices for using AWS Lambda. REPORT RequestId: 3604209a-e9a3-11e6-939a-754dd98c7be3 Duration: 12.34 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 18 MB
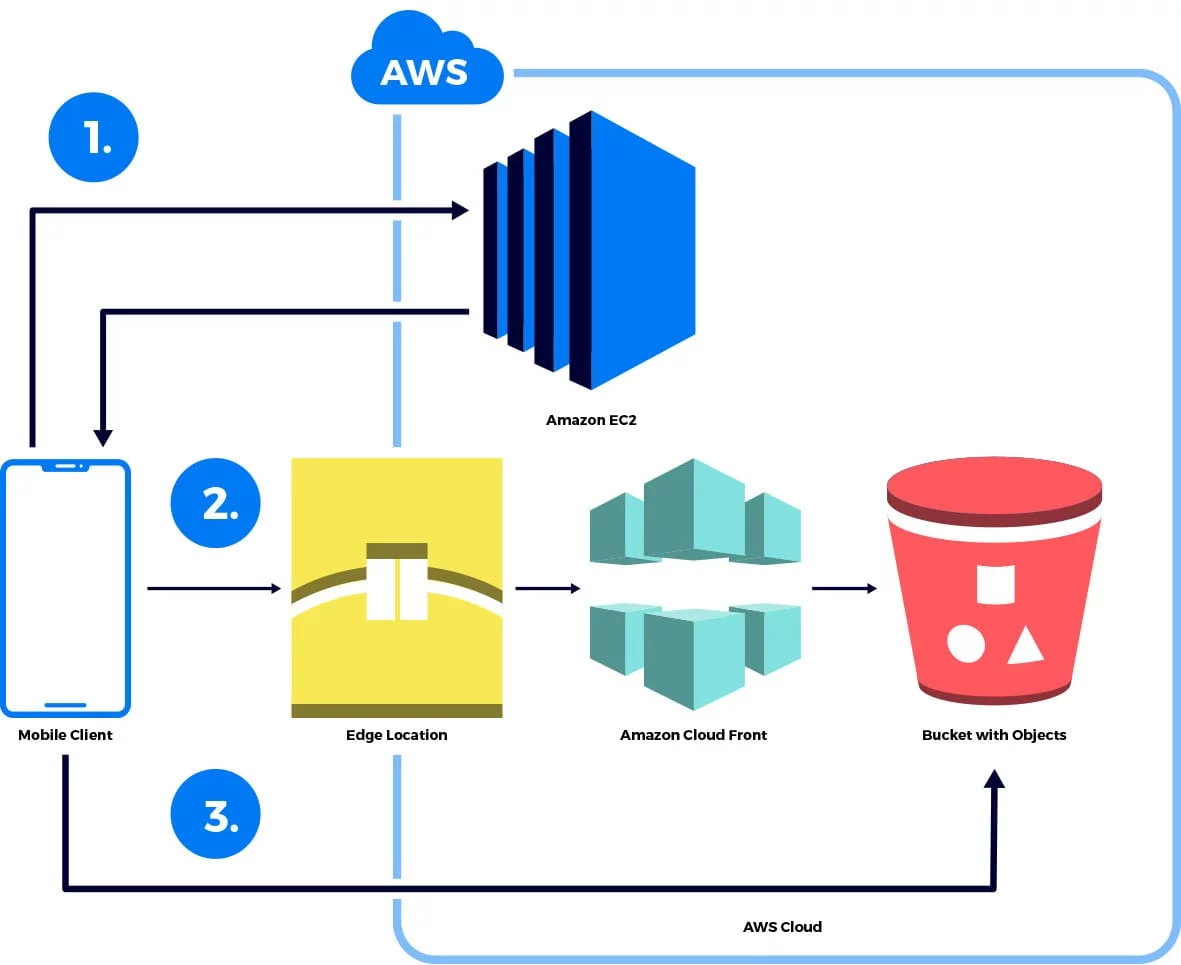
AWS Best Practices: five key approaches - Cloud Academy AWS Best Practices: secure your Applications, Sometimes it is better to explain a concept with a picture or diagram rather than with words. The diagram below could be a small scale deployment on AWS. You have a Web Server, an App Server, and a DB server. You should allow access from the outside world only where necessary.
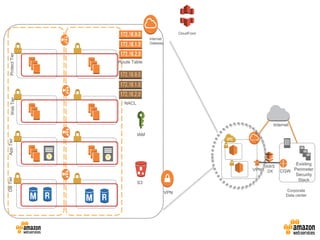
Aws best practices
4 AWS Security Best Practices - YouTube AWS provides a lot of built-in security attributes, making it a sought-after Infrastructure as a Service (IaaS) platform. It's a full-scale and developing cl... Best practices for managing AWS access keys For more information about best practices for AWS account security, see the following resources: IAM Best Practices contains suggestions that help you secure your AWS resources with the AWS Identity and Access Management (IAM) service. The following topics provide guidance when you set up the AWS SDKs and the AWS CLI to use access keys: ... docs.aws.amazon.com › general › latestBest practices for managing AWS access keys - AWS General ... IAM Best Practices contains suggestions that help you secure your AWS resources with the AWS Identity and Access Management (IAM) service. The following topics provide guidance when you set up the AWS SDKs and the AWS CLI to use access keys:
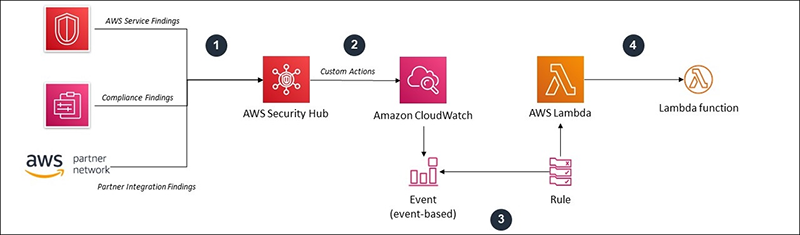
Aws best practices. Best practices for AWS accounts - AWS Account Management Best practices for AWS accounts, PDF, This section describes best practices that we recommend that you follow with your AWS accounts. They are arranged in the following categories: Topics, Best practices to protect your account's root user, Best practices for managing AWS access keys, Did this page help you? Provide feedback, Best Practices for AWS Organizations Service Control Policies in a ... Prevent users from disabling security tools like Amazon GuardDuty, AWS Config, AWS CloudTrail: This SCP prevents anyone from disabling the AWS security tools that are enabled as per best practices in various accounts. The SCP can allow only users in certain roles to be able to make these changes. Security best practices in IAM - AWS Identity and Access … Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide. AWS Foundational Security Best Practices standard The AWS Foundational Security Best Practices standard is a set of controls that detect when your deployed accounts and resources deviate from security best practices. The standard allows you to continuously evaluate all of your AWS accounts and workloads to quickly identify areas of deviation from best practices.
docs.aws.amazon.com › security-best-practicesSecurity Best Practices for Amazon S3 Amazon S3 provides a number of security features to consider as you develop and implement your own security policies. The following best practices are general guidelines and don’t represent a complete security solution. PDF Architecting for the loud Amazon Web Services - Architecting for the Cloud: AWS Best Practices Page 5 Design Principles The AWS Cloud includes many design patterns and architectural options that you can apply to a wide variety of use cases. Some key design principles of the AWS Cloud include scalability, disposable resources, automation, loose coupling managed services Establishing your best practice AWS environment The rest of this guide will walk you through the elements of building a secure and productive multi-account AWS environment, often referred to as a “landing zone,” as recommended by AWS. This represents the best practices that can be used to build an initial framework while still allowing for flexibility as your AWS workloads increase over ... AWS Best Practices for Beginners - Career Karma Learn AWS best practices to upskill in your cloud computing career. The cloud system is prone to security vulnerabilities. This is why it is important to master the AWS best practices to safeguard your AWS environment or data from security breaches. We curated a list of 10 AWS best practices and guidelines that will help improve your cloud ...
AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices. AWS Whitepaper. Welcome; AWS Documentation AWS Whitepapers AWS Whitepaper. AWS Security Best Practices. PDF RSS. Notice: This whitepaper has been archived. For the latest technical information on ... AWS Best Practices | Wharton Knowledge Base AWS Best Practices, Last Modified on 08/25/2022 10:48 am EDT, AWS is Wharton's preferred cloud vendor. Wharton has AWS Enterprise Support and has integrated account creation for AWS, allowing payment via budget code. For information on obtaining an account see AWS Linked Accounts. Table of Contents, Enterprise Support, Billing, User Access, Security Best Practices for Amazon S3 Enable AWS Config. Several of the best practices listed in this topic suggest creating AWS Config rules. AWS Config enables you to assess, audit, and evaluate the configurations of your AWS resources. AWS Config monitors resource configurations, allowing you to evaluate the recorded configurations against the desired secure configurations. AWS Identity and Access Management Best Practices To help secure your AWS resources, follow these IAM best practices. Use temporary credentials, Require human users to use federation with an identity provider to access AWS by using temporary credentials, Require your human users to rely on temporary credentials when accessing AWS.
Best practices when using Athena with AWS Glue - Amazon Athena When using Athena with the AWS Glue Data Catalog, you can use AWS Glue to create databases and tables (schema) to be queried in Athena, or you can use Athena to create schema and then use them in AWS Glue and related services. This topic provides considerations and best practices when using either method.
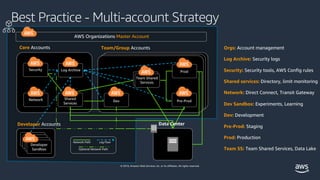
Best Practices for Organizational Units with AWS Organizations Jul 21, 2020 · Best practices for setting up your multi-account AWS environment Before getting started, let’s get familiar with a few terms. An organizational unit (OU) is a logical grouping of accounts in your organization, created using AWS Organizations.
Best practices for Amazon EC2 - Amazon Elastic Compute Cloud How the AWS binary blob is created, Find a Linux AMI, Shared AMIs, Find shared AMIs, Make an AMI public, Share an AMI with organizations or OUs, Share an AMI with specific AWS accounts, Use bookmarks, Guidelines for shared Linux AMIs, Paid AMIs, AMI lifecycle, Create an AMI, Create an Amazon EBS-backed Linux AMI,
Getting Started: Follow Security Best Practices as You Configure Your ... Best practices to help secure your AWS resources, When you created an AWS account, you specified an email address and password you use to sign in to the AWS Management Console. When you sign in using these credentials, you are accessing the console by using your root account.
docs.aws.amazon.com › IAM › latestSecurity best practices in IAM - AWS Identity and Access ... To help secure your AWS resources, follow these best practices for AWS Identity and Access Management (IAM) . Topics, Require human users to use federation with an identity provider to access AWS using temporary credentials, Require workloads to use temporary credentials with IAM roles to access AWS, Require multi-factor authentication (MFA)
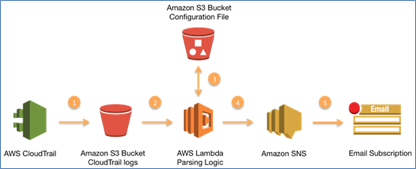
How To Make Light Work Of AWS IAM Best Practices The last of the AWS IAM best practices relates to monitoring activity on your AWS account to identify anomalies and make changes where required. AWS recommends using a mixture of Amazon CloudFront, AWS CloudTrail, Amazon CloudWatch, AWS Config, and Amazon S3 logs to observe the dates and times of users' actions, the source IP of specific ...
AWS Foundational Security Best Practices standard The AWS Foundational Security Best Practices standard is a set of controls that detect when your deployed accounts and resources deviate from security best practices. The standard allows you to continuously evaluate all of your AWS accounts and workloads to quickly identify areas of deviation from best practices.
Best practices for AWS Organizations - AWS Organizations Best practices for AWS Organizations - AWS Organizations, AWS, Documentation, AWS Organizations, User Guide, Best practices for AWS Organizations, PDF RSS, We recommend that you follow these best practices when you create and operate your organization. Topics, Best practices for the management account, Best practices for member accounts,
docs.aws.amazon.com › lambda › latestBest practices for working with AWS Lambda functions Best practices for using AWS Lambda. REPORT RequestId: 3604209a-e9a3-11e6-939a-754dd98c7be3 Duration: 12.34 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 18 MB
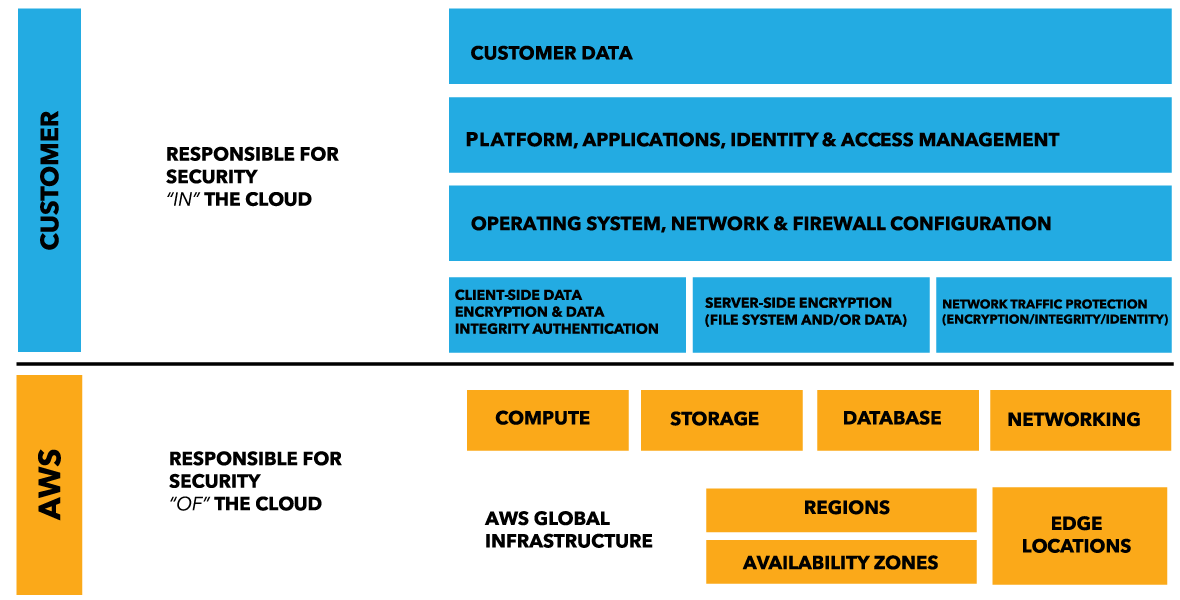
PDF AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 2 Know the AWS Shared Responsibility Model Amazon Web Services provides a secure global infrastructure and services in the cloud. You can build your systems using AWS as the foundation, and architect an ISMS that takes advantage of AWS features.
Amazon ECS availability best practices | Containers Nov 08, 2019 · At AWS, we think about availability a great deal and work hard to provide customers with the tooling needed to make achieving availability as simple as possible. It is however important to understand the best practices on which these tools are based and the nuances of the tools in order to ensure the best possible availability for your service.
AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance After all the effort, it would be silly not to utilize AWS Config, or a time-saving alternative like Hyperglance, to make sure that your best practices stay that way. The best-in-class cloud security tools include hundreds of rule-based checks (here are Hyperglance's security checks as an example). Also, look out for codeless implementations ...
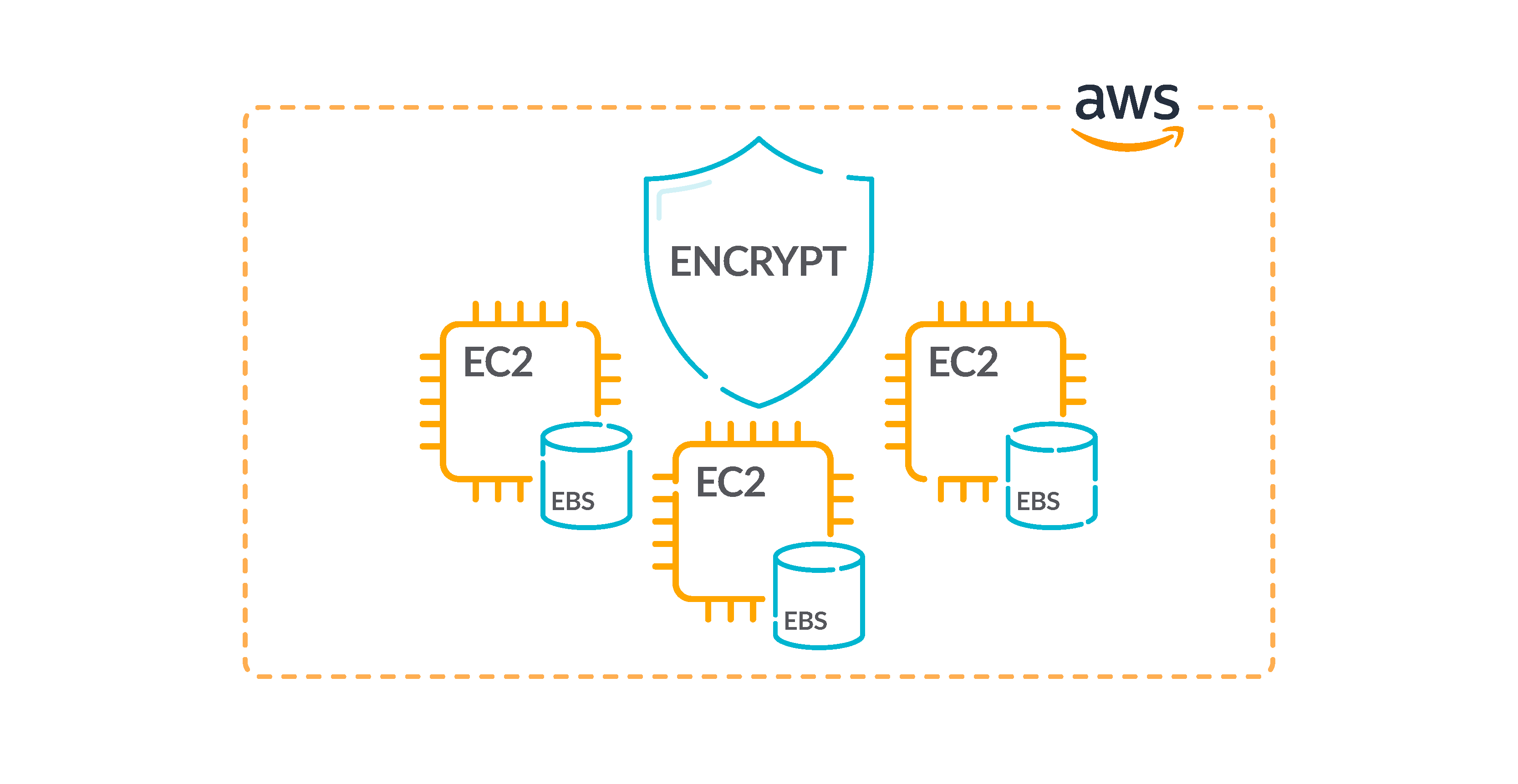
AWS CloudTrail Security Best Practices to Keep in Mind Best practices for AWS CloudTrail security. When any kind of data is stored, security is almost always the hottest concern (as it should be.) By default, CloudTrail keeps log files encrypted using Amazon S3 Server Side Encryption (SSE). However, the bigger part of the responsibility falls on your shoulders, including:
PDF Silver Peak Best Practice Guidelines: AWS Transit Gateway This document provides design guidance and best practices for extending the Silver Peak Unity EdgeConnect SD-WAN fabric into a multi-region AWS network using AWS Transit Gateways. Overview Silver Peak Unity EdgeConnect is available as a Bring your own License (BYOL) AMI in the AWS marketplace. For
AWS DynamoDB Best Practices: 10 Tips to Maximize Performance 10 DynamoDB Best practices. 1. Identify your application's access patterns. First off, working with DynamoDb requires a mindset shift to NoSQL design. You design the schema specifically to make the most important and common queries as fast and inexpensive as possible.
Best practices for monitoring - Amazon Elastic Compute Cloud Make monitoring a priority to head off small problems before they become big ones. Create and implement a monitoring plan that collects monitoring data from all of the parts in your AWS solution so that you can more easily debug a multi-point failure if one occurs. Your monitoring plan should address, at a minimum, the following questions:
aws.amazon.com › security-best-practicesLearn best practices for securing your AWS account and resources Here are some best practices to consider when securing your account and its resources: Safeguard your passwords and access keys, Activate multi-factor authentication (MFA) on the AWS account root user and any users with interactive access to AWS Identity and Access Management (IAM) Limit AWS account root user access to your resources,
Best Practices | AWS Marketplace Best practices for driving traffic to your AWS Marketplace listing, In this blog post, I will share AWS programs and resources you can use to increase awareness and drive traffic to your AWS Marketplace listings. AWS Marketplace is a curated digital software catalog that lets AWS customers find, test, and purchase third-party software licenses.
aws.amazon.com › getting-started › best-practicesEstablishing your best practice AWS environment The rest of this guide will walk you through the elements of building a secure and productive multi-account AWS environment, often referred to as a “landing zone,” as recommended by AWS. This represents the best practices that can be used to build an initial framework while still allowing for flexibility as your AWS workloads increase over ...
Learn best practices for securing your AWS account and resources Aug 22, 2022 · For more information, see Security best practices in AWS CloudTrail. Use CloudTrail and CloudWatch in conjunction to monitor access key usage and receive alerts for unusual API calls. Activate resource-level logging (for example, at the instance or OS level) and Amazon S3 default bucket encryption.
docs.aws.amazon.com › general › latestBest practices for managing AWS access keys - AWS General ... IAM Best Practices contains suggestions that help you secure your AWS resources with the AWS Identity and Access Management (IAM) service. The following topics provide guidance when you set up the AWS SDKs and the AWS CLI to use access keys:
Best practices for managing AWS access keys For more information about best practices for AWS account security, see the following resources: IAM Best Practices contains suggestions that help you secure your AWS resources with the AWS Identity and Access Management (IAM) service. The following topics provide guidance when you set up the AWS SDKs and the AWS CLI to use access keys: ...
4 AWS Security Best Practices - YouTube AWS provides a lot of built-in security attributes, making it a sought-after Infrastructure as a Service (IaaS) platform. It's a full-scale and developing cl...

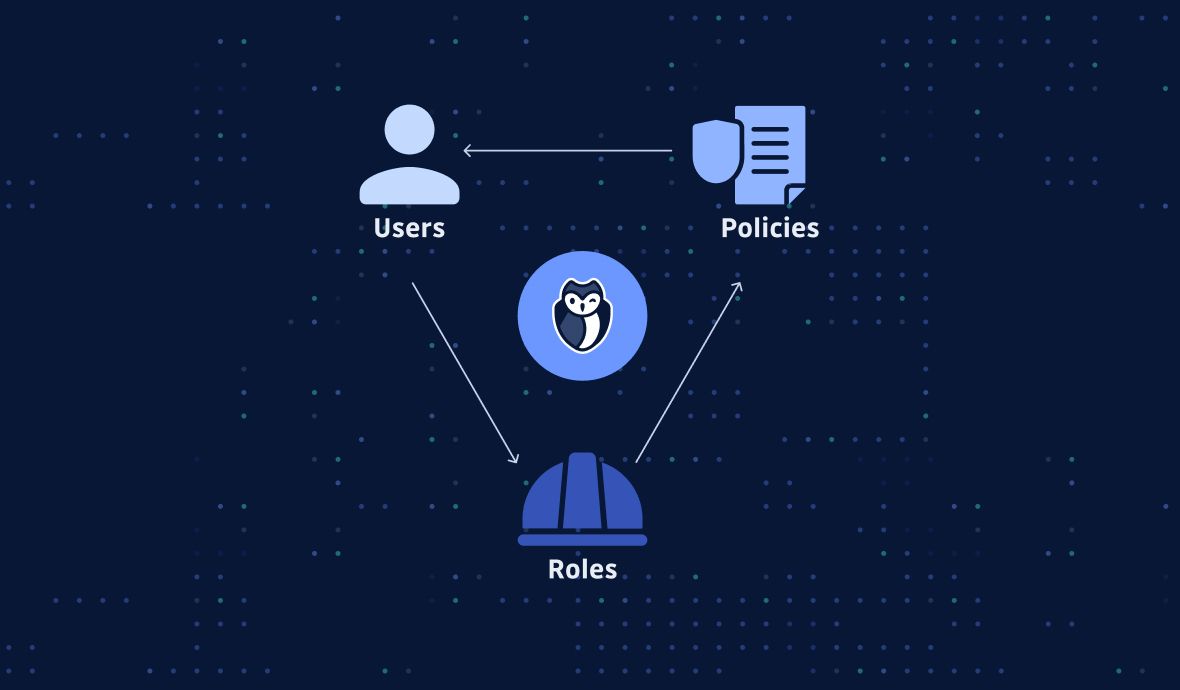

























0 Response to "39 aws best practices"
Post a Comment